ALPHV Story:
1. The malware was first observed by researchers from the MalwareHunterTeam in mid-November 2021.2. In September 2022, a report noted that the ransomware was using the Emotet botnet.
3. In late May 2022, a European government was attacked and asked US$5 million in ransom.
ALPHV Seizure:
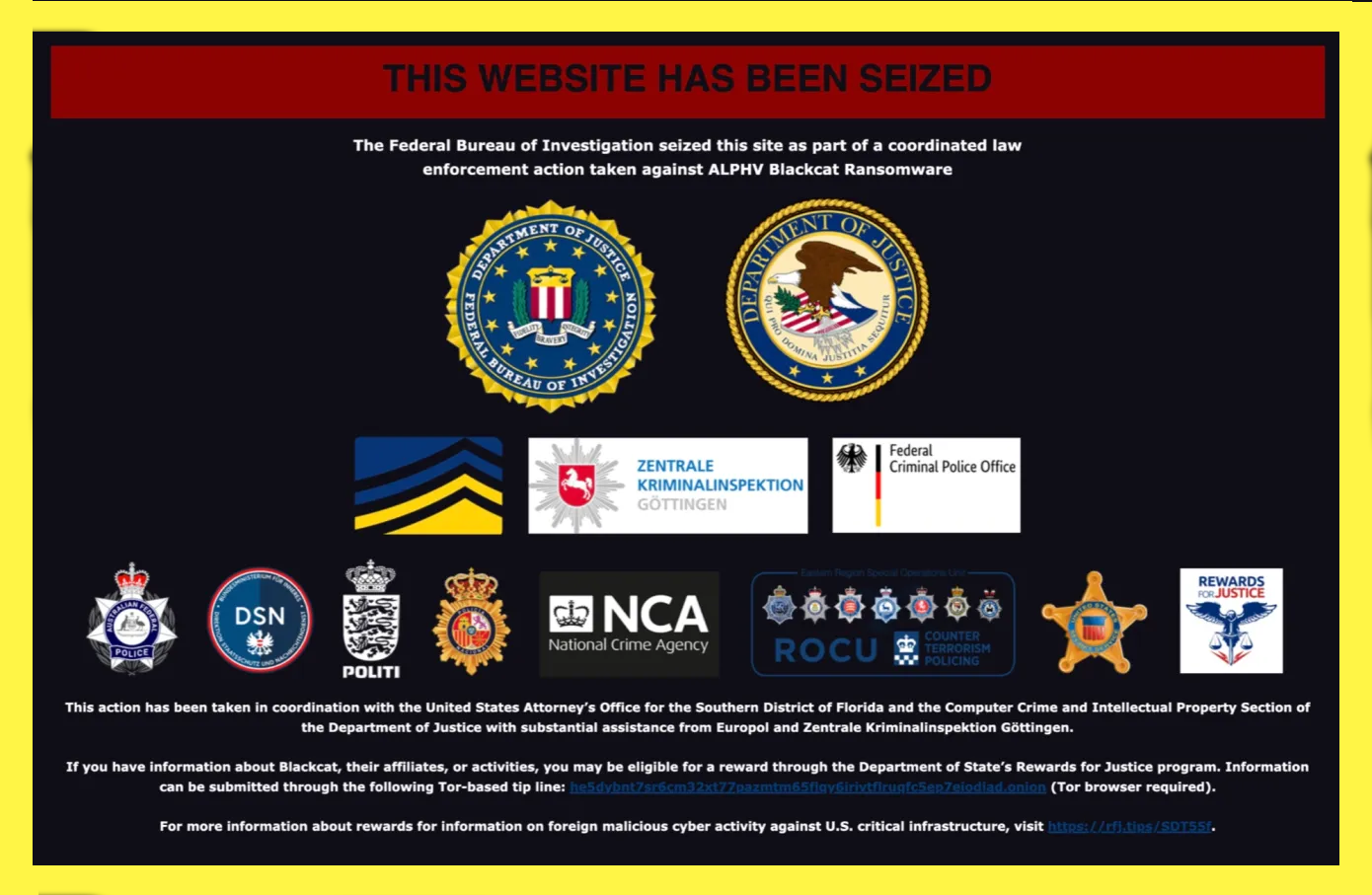
An international consortium of law enforcement agencies has successfully confiscated the dark web leak site belonging to the infamous ransomware gang, ALPHV, also known as BlackCat.
"BlackCat, alternatively recognized as ALPHV and Noberus, is a ransomware strain coded in Rust, which emerged for the first time in November 2021. Moreover, it serves as the designation for the threat actor responsible for its exploitation. BlackCat functions on a ransomware as a service framework (RaaS), wherein developers provide the malware to affiliates for utilization, while retaining a portion of the ransom payments as compensation." source - Wikipedia.org
A message displayed on the gang's dark web leak site, as observed by TechCrunch, states that the Federal Bureau of Investigation has taken control of the site as part of a meticulously coordinated law enforcement initiative targeting ALPHV Blackcat Ransomware.
The aforementioned operation, as indicated by the announcement, was executed in collaboration with international law enforcement agencies from the United Kingdom, Denmark, Germany, Spain, and Australia.
Government's Declaration:
In a subsequent statement confirming the disruption, the U.S. Department of Justice declared that the international operation, spearheaded by the FBI, facilitated the acquisition of insight into the computer systems of the ransomware group, ALPHV, resulting in the seizure of "several websites".
Furthermore, the FBI has released a decryption tool that has already enabled over 500 victims of ALPHV ransomware to restore their systems. (According to the government's search warrant, the number of victims stands at 400.) The FBI collaborated with numerous victims in the United States, thereby preventing them from succumbing to ransom demands amounting to approximately $68 million.
According to the government's announcement, ALPHV infiltrated the networks of more than 1,000 victims worldwide, amassing hundreds of millions of dollars. The gang specifically targeted critical infrastructure within the United States, including government facilities, emergency services, defense industrial base companies, critical manufacturing, healthcare and public health facilities, as well as various corporations, educational institutions, and government entities, as stated by the DOJ.

Witch Hunt Continues:
The Department of State has previously announced its intention to provide rewards to individuals who provide information regarding Blackcat, its affiliates, or its activities.
In her statement, U.S. Deputy Attorney General Lisa Monaco expressed that the Justice Department has successfully disrupted the BlackCat ransomware group, effectively hacking the hackers. Through the provision of a decryption tool by the FBI to numerous ransomware victims globally, businesses and educational institutions were able to resume operations, while healthcare and emergency services were able to restore their online presence. The prioritization of disruptions and the focus on placing victims at the core of our strategy aim to dismantle the ecosystem that fuels cybercrime.
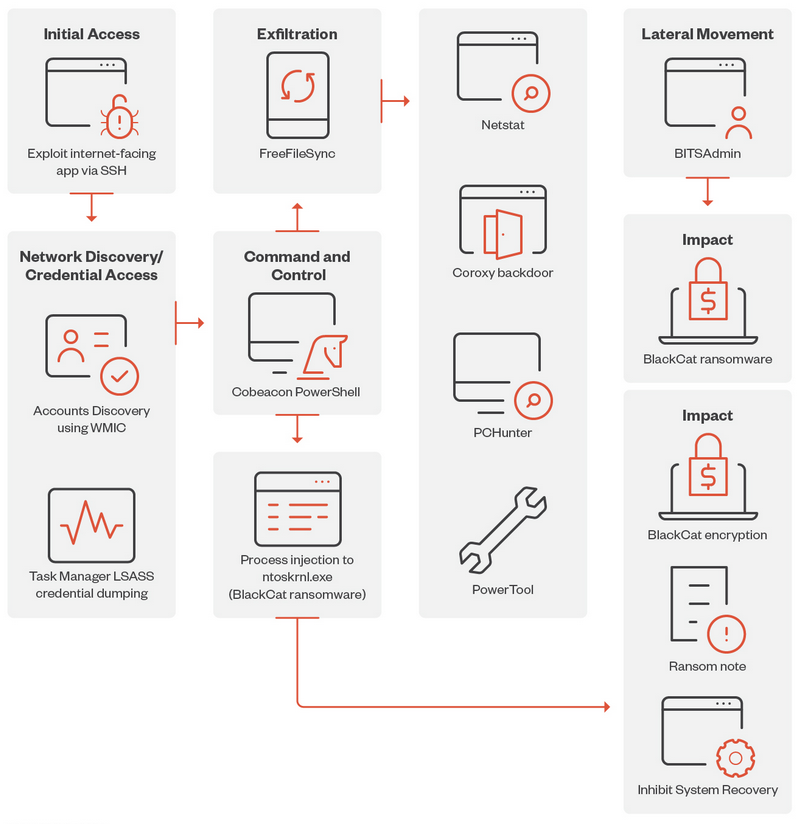
Deduction:
The ALPHV/BlackCat ransomware gang has emerged as one of the most active and destructive cybercriminal organizations in recent times. It is widely believed to be a successor to the now-defunct REvil hacking group, which was subject to sanctions. ALPHV boasts about successfully infiltrating several prominent targets, including Reddit, a popular news-sharing platform, Norton, a healthcare company, and the Barts Health NHS Trust in the United Kingdom.
In recent months, the group has adopted increasingly aggressive tactics. Notably, in November, ALPHV took an unprecedented step by lodging a complaint with the U.S. Securities and Exchange Commission (SEC). The complaint alleged that MeridianLink, a digital lending provider, had failed to disclose a significant breach that compromised customer data and operational information. The gang claimed responsibility for this breach and sought recognition for their actions.
Goodbye:
I hope you enjoyed diving into our latest article as much as I enjoyed bringing it to you!