Latin American users who speak Spanish have been targeted by a newly discovered botnet malware known as Horabot since at least November of 2020.
According to Chetan Raghuprasad, a researcher at Cisco Talos, Horabot facilitates the ability of the threat actor to manipulate the Outlook mailbox of the victim, extract email addresses of contacts, and distribute phishing emails containing harmful HTML attachments to all addresses present in the victim's mailbox.
The botnet program additionally dispenses a Windows-based financial trojan and a spam tool to gather online banking credentials, along with compromising Gmail, Outlook, and Yahoo! webmail accounts to disseminate spam emails. As per the cybersecurity firm's report, a significant number of infections have been detected in Mexico, with a few victims identified in Uruguay, Brazil, Venezuela, Argentina, Guatemala, and Panama. The perpetrator responsible for the campaign is suspected to be located in Brazil.
The current campaign is primarily aimed at users in the accounting, construction, engineering, wholesale distribution, and investment sectors. However, it is believed that other industries in the region may also be impacted.
The onset of the attacks commences with the dissemination of phishing emails that bear tax-themed attachments, aimed at inducing the recipients to open an HTML attachment. This attachment, in turn, embeds a link that contains a RAR archive.
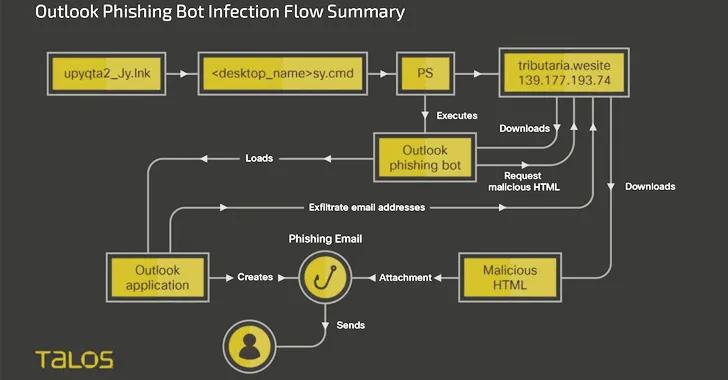
Upon opening the contents of the file, a PowerShell downloader script is executed, which is responsible for retrieving a ZIP file containing the primary payloads from a remote server and initiating a system restart.
The system restart serves as a launchpad for the banking trojan and the spam tool, enabling the threat actor to pilfer data, log keystrokes, capture screenshots, and disseminate additional phishing emails to the victim's contacts.
Raghuprasad stated that the campaign entails a multi-stage attack chain, which commences with a phishing email and culminates in payload delivery via the execution of a PowerShell downloader script and sideloading to legitimate executables.
The banking trojan is a 32-bit Windows DLL that has been authored in the Delphi programming language. It exhibits similarities with other Brazilian malware families such as Mekotio and Casbaneiro.
On the other hand, Horabot is an Outlook phishing botnet program that has been scripted in PowerShell. It possesses the ability to dispatch phishing emails to all email addresses present in the victim's mailbox, thereby facilitating the spread of the infection. Furthermore, it is a calculated endeavor to reduce the likelihood of the threat actor's phishing infrastructure being uncovered.
The aforementioned disclosure has been made one week subsequent to SentinelOne's attribution of an unknown Brazilian threat actor to a protracted campaign aimed at over 30 Portuguese financial institutions, utilizing information-stealing malware since 2021. Furthermore, the disclosure follows the identification of a new Android banking trojan, PixBankBot, which exploits the accessibility services of the operating system to execute fraudulent money transfers via the Brazilian PIX payments platform. PixBankBot is the most recent instance of malware that specifically targets Brazilian banks, exhibiting similar capabilities to BrasDex, PixPirate, and GoatRAT, which have been observed in recent months. These developments are indicative of a broader group of financially motivated hacking endeavors originating from Brazil, underscoring the importance of user vigilance in order to avoid falling victim to such threats.




