During the course of your exploration of the dark web, you may have encountered the term 'multisig'. Today, we will try to demistify and explain its meaning, in order to facilitate a more comprehensive understanding of the workings of the darknet markets.
Why is multisig used on the darkweb markets
In the domain of darknet markets, the utmost importance is placed on security and trust by both buyers and sellers. Conventional payment modes, such as credit cards or bank transfers, are fraught with risk owing to the possibility of identity disclosure. Nevertheless, the emergence of cryptocurrencies, particularly Bitcoin and Monero, has presented a more secure option for carrying out darknet transactions. Nonetheless, the intrinsic anonymity of cryptocurrencies does not ensure absolute safety.
In order to mitigate these concerns and bolster security within the darknet market ecosystem, the technology of multisig has arisen. Multisig, an abbreviation for multi-signature, is a cryptographic instrument that enables multiple parties to jointly manage a single cryptocurrency address. This technology not only provides an extra level of security, but also fosters a sense of confidence among parties engaging in transactions.
The objective of this article is to examine the utilization of multisig technology in darknet markets, with a particular emphasis on its ability to augment security and trust in illicit online transactions. Our analysis will encompass an in-depth exploration of the workings of darknet markets, an elucidation of the concept of multisig technology, a discussion of its advantages and drawbacks, and an evaluation of actual case studies. Additionally, we will scrutinize the legal and ethical ramifications of the employment of multisig technology in darknet markets, as well as potential future developments and challenges.
Downsides of multisig
Although multisig transactions offer heightened security and control, they do present certain drawbacks. One such disadvantage is the increased complexity associated with establishing and managing multisig wallets. This process necessitates coordination among multiple parties, each of whom possesses their own private key. This complexity may dissuade users who lack technical expertise or familiarity with multisig functionality. Furthermore, multisig transactions may prove more time-consuming and resource-intensive, as they require the gathering of multiple signatures for each transaction. This may not be suitable for scenarios that require swift and efficient transfers. Additionally, if one of the parties involved loses their private key or becomes unresponsive, it can create complications and impede the execution of transactions. Finally, the involvement of multiple parties introduces the possibility of disagreements and disputes, which can prolong the transaction process and potentially necessitate third-party (in case of darknet markets intervention from the administrators of the market) intervention for resolution.
2/3 vs 3/3 multisig configurations
In the realm of multisig transactions, whether within darknet markets or any other context, two commonly utilized configurations are the 2/3 and 3/3 multisig setups. The primary distinction between the two lies in the number of signatures required to authorize a transaction. In a 2/3 multisig setup, two out of three possible signatures are necessary to proceed with a transaction. This configuration provides an additional layer of security by mandating multiple parties to approve the transaction, thereby reducing the risk of a single compromised private key leading to unauthorized transfers. Conversely, in a 3/3 multisig setup, all three parties must provide their signatures to authorize a transaction, making it an even more secure option. The added requirement of all parties ensures that no single participant can independently initiate a transaction, thereby enhancing trust and mitigating the chances of fraudulent or unauthorized activities. However, the choice between 2/3 and 3/3 multisig ultimately depends on the specific needs and risk tolerance of the parties involved. It is noteworthy that traditionally, darknet markets have employed the 2/3 multisig setup.
Dispute handling in 2/3 multisig transactions
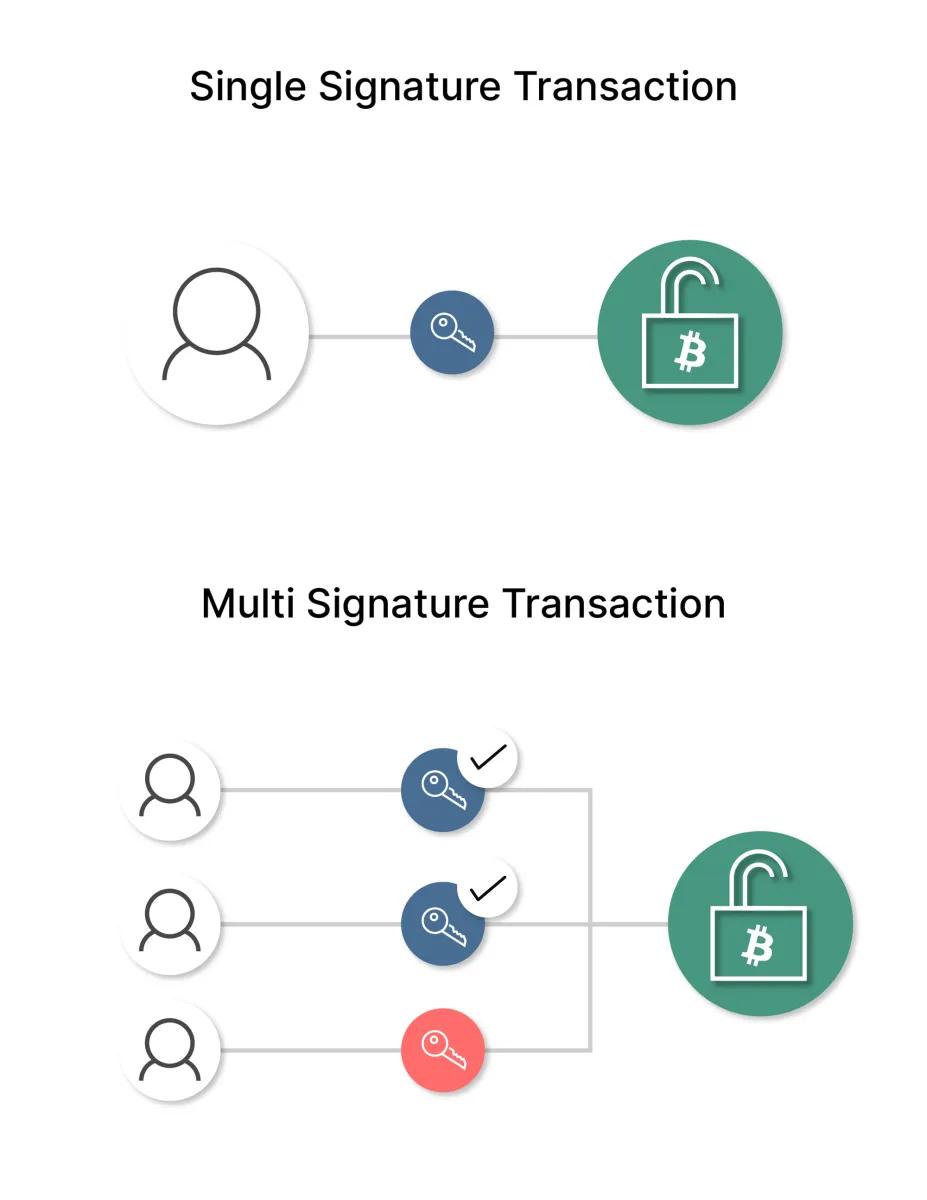
In a 2/3 multisig transaction, three parties are engaged, each possessing their own private key. In order to initiate a transaction, two out of the three parties must provide their signatures. This configuration guarantees that the transaction is not reliant on the authorization of a single individual, thereby effectively mitigating the risk of unauthorized transfers or fraudulent activity. In the event of a dispute arising during a 2/3 multisig transaction, where one party dissents from the transaction, there are two potential avenues for resolution. Firstly, the involved parties may endeavor to reach a consensus and identify a mutually acceptable resolution. Should this prove unsuccessful, the dispute resolution process will involve an administrator of the darknet market. These administrators will serve as mediators or make the final determination as to whether the transaction should proceed or be cancelled, based on the circumstances and the terms agreed upon by the parties involved. This approach provides an additional layer of security and facilitates equitable resolution in the event of conflicts or disagreements in a 2/3 multisig transaction scenario.
Conclusion
It is recommended that individuals utilizing the Darknet consider the utilization of multisig transactions as a means of enhancing their security and anonymity. Multisig transactions offer an additional layer of protection by necessitating the authorization of a transaction through multiple private keys, thereby reducing the risk of theft or fraud. This feature can effectively prevent unauthorized access to funds, making it more difficult for hackers or law enforcement agencies to compromise the user's identity or seize their assets. By distributing the signing power among multiple parties, multisig transactions further limit the potential for a single point of failure or vulnerability. It is important to note, however, that while multisig adds security, it does not guarantee complete anonymity. Darknet users should exercise caution and employ additional privacy measures such as using VPNs, Tor networks, and encrypted messaging to mitigate risks. Additionally, the increased complexity and potentially slower transaction process of multisig may not be suitable for all darknet users who prioritize convenience and speed over enhanced security.




