The internet, in its current form, encompasses an extensive array of websites, platforms, and services. However, there exists a concealed enclave, beyond the purview of mainstream visibility, commonly referred to as the dark web. The objective of this article is to delve into the technologies that facilitate the existence of the dark web, unraveling the intricate layers of privacy, encryption, and anonymization.
Tor Network: The Gateway to the Dark Web
The Tor network, abbreviated for "The Onion Router," is situated at the core of the dark web. It is a decentralized network of servers that facilitates users to access the internet, comprising the concealed services of the dark web, with a significant level of anonymity. This is accomplished by directing user traffic through numerous servers, encrypting it at each stage, and concealing the source IP address.
Onion Services: Concealing Identities
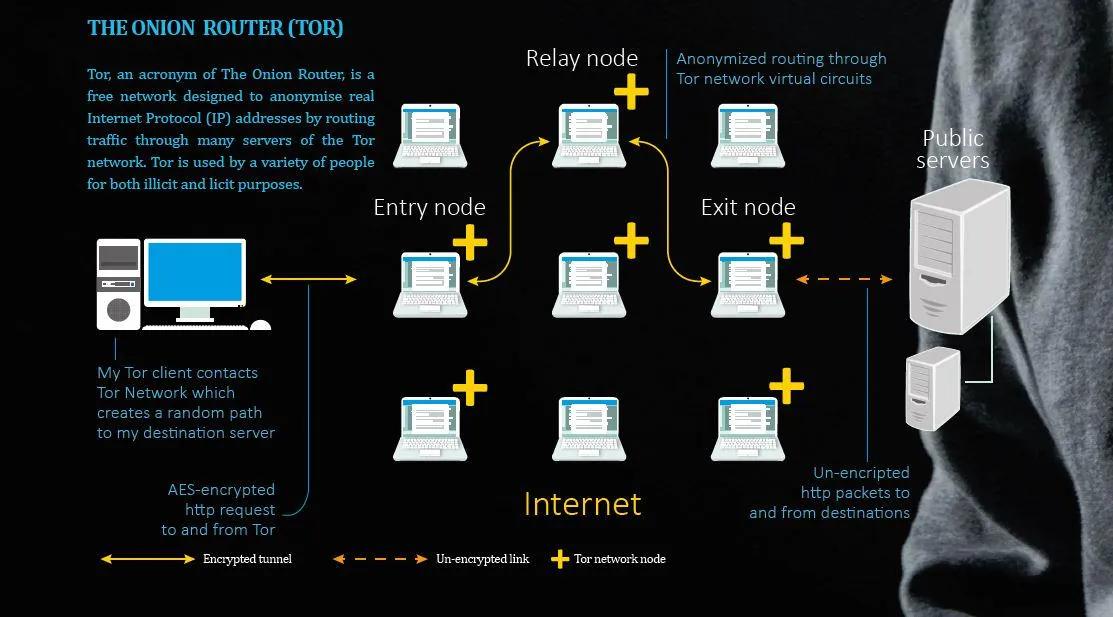
Onion services, commonly referred to as hidden services, serve as a crucial component in upholding the privacy and anonymity of the dark web. These online platforms or websites are exclusively accessible via the Tor network, and their domain names conclude with the ".onion" extension, thereby guaranteeing their concealment from conventional search engines and external examination. The encryption and anonymization mechanisms offered by onion services pose a formidable obstacle in identifying the proprietors or users of these sites.
Cryptocurrencies: Anonymous Transactions
Cryptocurrencies, such as Bitcoin, have emerged as the favored means of conducting financial transactions on the dark web, particularly within dark web markets. These digital currencies provide a degree of anonymity and decentralization that conventional payment methods are unable to offer. Transactions executed through cryptocurrencies are arduous to trace, as they do not disclose any personal information pertaining to the sender or receiver. This serves to augment the surreptitious character of dark web operations, encompassing the procurement and vending of illicit commodities.
Encryption: Protecting Communication
Encryption is a pivotal technology that is extensively employed in diverse domains of the dark web. Its primary function is to guarantee the confidentiality and protection of communications, encompassing messages, file transfers, and browsing activities, from unauthorized access. The prevalent practice of end-to-end encryption is adopted, whereby solely the sender and the designated recipient possess the capability to decrypt the transmitted data, rendering it arduous for any third party to intercept or decipher the information.
Pseudonyms and Forums: Community Building
Pseudonyms, commonly known as anonymous usernames, are widely utilized in dark web platforms and communities. These usernames serve as the unique identity of individuals, promoting a sense of community and interaction while safeguarding the anonymity of users. Dark web forums function as virtual gathering spots where users can engage in discussions on a diverse range of subjects, encompassing illicit activities, knowledge sharing, and even extending support to individuals with similar interests.
Decentralization: Evading Censorship and Monitoring
The decentralized structure of the dark web guarantees that no singular entity possesses authority over its operations. This decentralization poses a formidable obstacle for governmental and law enforcement agencies seeking to effectively regulate or dismantle the dark web. Hosting services, domain name systems, and data storage are dispersed across numerous servers, rendering it arduous to identify the location or jurisdiction of dark web entities.
Conclusion
The dark web is a fascinating and enigmatic domain that depends on advanced technologies to sustain its elusive presence. The Tor network, onion services, cryptocurrencies, encryption, pseudonyms, and decentralization are among the technologies that jointly contribute to the anonymity and confidentiality that users and service providers enjoy. Although these technologies give rise to apprehensions about unlawful activities, they also stimulate debates about the significance of online privacy and the function of technology in safeguarding individual freedoms in a progressively interconnected world.

